Here's New Year's first Ransomware: Ransom32.
A new Ransomware-as-a-service, dubbed Ransom32, has been spotted that for the first time uses a ransomware written in JavaScript to infect Mac, Windows as well as Linux machines.
Ransom32 allows its operators to deploy the malware very quickly and easily. It has a dashboard that enables operators to designate their Bitcoin addresses to which the ransom can be sent. The dashboard also shows stats about how much Bitcoins they have made.
In short, this new ransomware-as-a-service is so simple, and efficient at the same time, that anyone can download and distribute his/her own copy of the ransomware executable as long as he/she have a Bitcoin address.
The copy of Ransom32 was first analysed by Emsisoft, which found that the new ransomware family, which embedded in a self-extracting WinRAR archive, is using the NW.js platform for infiltrating the victims' computers, and then holding their files by encrypting them with 128-bit AES encryption.
But, Why the NW.js Framework?
NW.js, formerly known as Node-WebKit, is a JavaScript framework for app development based on Node.js and Chromium. It works around normally-strict sandboxing of JavaScript, so a Web app can be repurposed for desktops without the sandbox getting in its way.
"NW.js allows for much more control and interaction with the underlying operating system (OS), enabling JavaScript to do almost everything 'normal' programming languages like C++ or Delphi can do," Emsisoft's Fabian Wosar writes.
The NW.js framework not only allows for cross-platform infections but also is harder to detect because it is a legitimate framework. Ransom32 has some resemblance to CryptoLocker that is one of the nasty ransomware that already infected millions of PCs.
Ransom32 has been traded on the dark web with the authors asking for a 25 percent cut of all ransom payments for offering its service and forwarding the rest of the amount to the operator’s Bitcoin address.
How Does Ransom32 Work?
Malware operators place the malicious file inside emails masquerading as delivery notifications, unpaid invoices, and such.
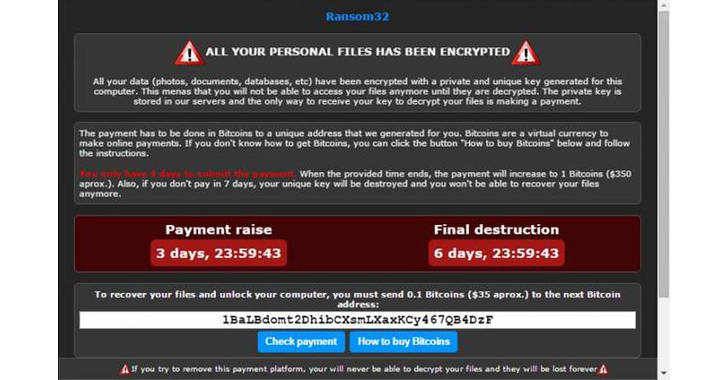
As soon as it was installed and launched, Ransom32 connected to a command-and-control (C&C) server on TOR anonymising network, displaying ransom note as shown above and the Bitcoin address where victims are supposed to pay to recover their files.
Currently, Wosar has only seen Ransom32 as a Windows attack vector, but the NW.js framework can run on all three major operating systems.
Therefore, ransomware coded to work on top of NW.js would theoretically be able to target Mac OS X as well as Linux operating systems.
How to Protect Yourself from Ransomware Threat?
Here are some important steps that should be considered to protect yourself from Ransomware threats.
- Always keep regular backups of your important data.
- Make sure you run an active anti-virus security suite of tools on your system.
- Do not open email attachments from unknown sources.
- Most importantly, always browse the Internet safely



0 comments:
Post a Comment